D-ECS
D-Link Remote Management Platform
Status Monitoring & Alerts
Track device status and traffic usage continuously with customizable alert thresholds for rapid issue response.
Traffic Report for Data Analysis
View detailed traffic data including cellular signal strength, data usage, and LAN activity for smarter decisions.
View Connected Client Lists
View the Ethernet or wireless connected client lists which are the application devices that your customers care about.
Routine Maintenance Scheduled Tasks
Schedule routine maintenance tasks for specified batch devices and during off-peak hours to avoid service interruption.
Geo-Location with Google Maps
Track device locations globally using Google Maps with live status indicators for all online and offline devices.
Floor Plan Management
Visualize M2M device status and placement on custom floor plans to simplify on-site service and management
Multi-Tenant Role-Based Access Control
Manage user permissions by role across organizations securely, reducing access complexity and risk.
Built-in Diagnostic Tools
Identify and resolve network issues using integrated tools like ping and trace route, for fast troubleshooting.
Productivity
Enhanced Business Operation
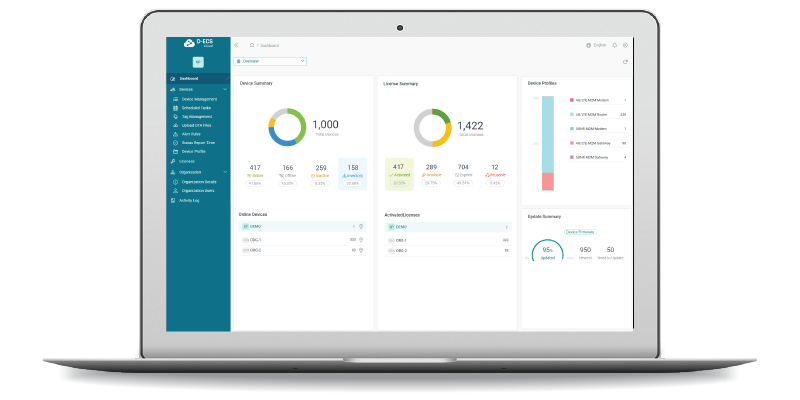
Monitor all device statuses and controls from a centralized dashboard, reducing time spent switching between systems.
Device & License Overview
Instantly view total device and license counts without extra admin effort, keeping you informed at a glance.
Device Grouping & Tag Management
Easily organize and filter devices using custom tags and groups for more efficient monitoring and streamlined operations.
Automated Tasks Scheduling
Plan firmware updates, reboots, and other tasks in bulk during off-peak hours to reduce downtime and maintain performance.
Built-in Diagnostic Tools
Identify and resolve connectivity issues fast with integrated tools like ping and trace route—reducing downtime and ensuring smooth, uninterrupted operations.
Insight
Improved Decision-Making
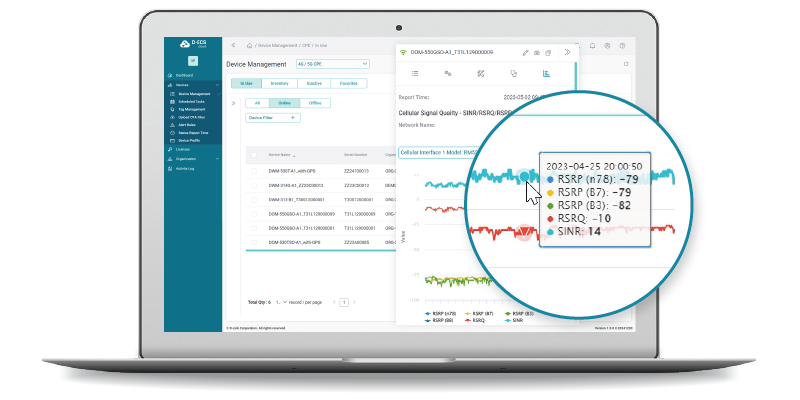
Provide continuous monitoring of cellular signal quality (SINR, RSRQ, RSRP), network usage (Cellular, LAN, Wi-Fi), and overall connectivity status. Users can visualize trends and download data for further analysis.
View Client Lists
Allows you to monitor devices connected via Ethernet or wireless without interfering with your customers' dedicated business applications. Easily review the list of end-client devices that your customers care about.
Alert Rules & Notifications
Set up customizable alert rules to monitor traffic usage and device connectivity. Receive e-mail notifications when predefined thresholds are exceeded, ensuring proactive network monitoring and minimal downtime.
Visibility
Network Status as a Glance
Track and manage device locations with positioning and node status displayed on an interactive map.
Floor Plan View
Visually monitor device connectivity and status on your customized floor plan for easy management and faster maintenance.

Security
Protect Your M2M Devices with Trusted, End-to-End Security
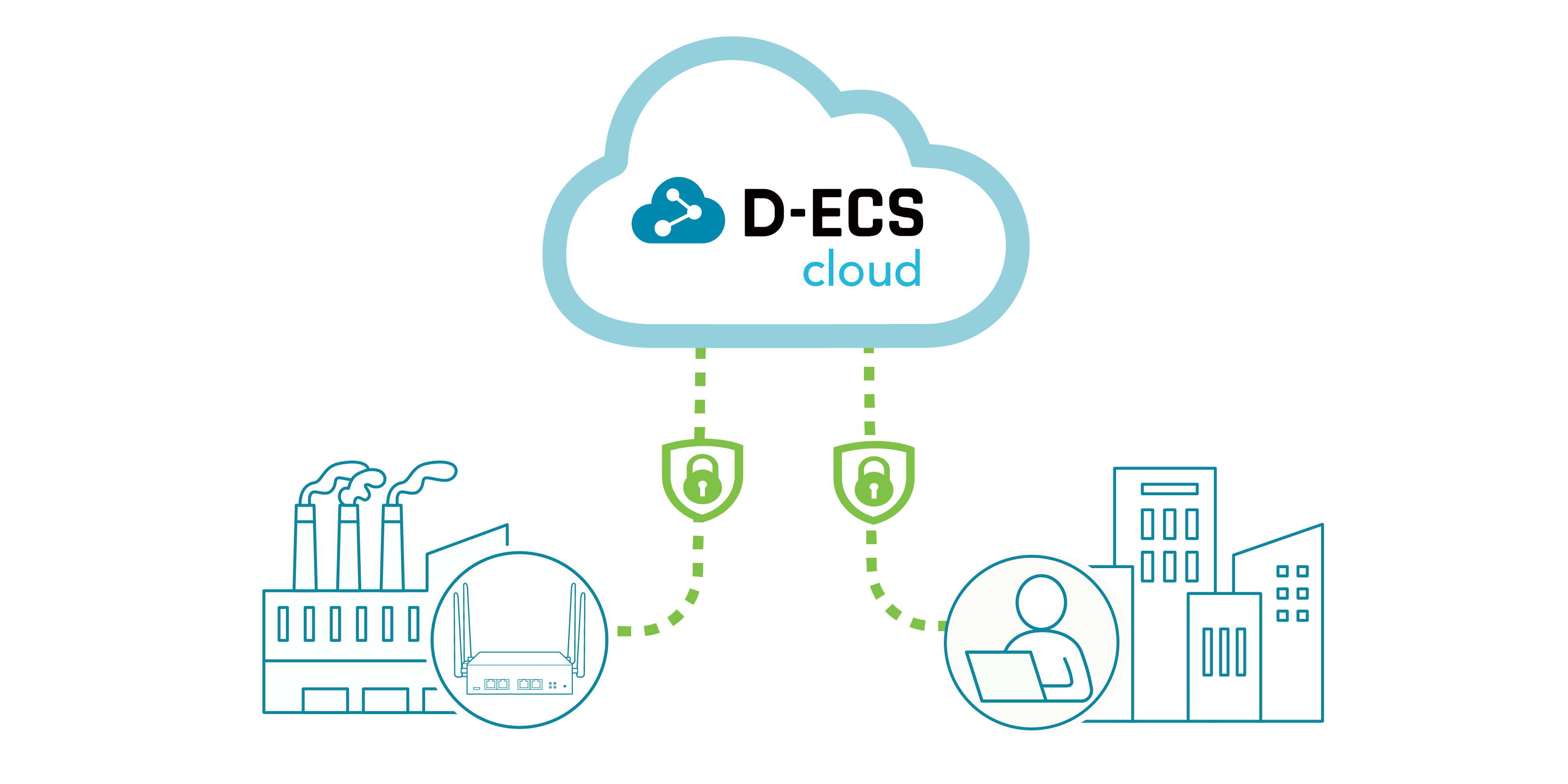
D-ECS is hosted on Amazon Web Services (AWS), delivering world-class cloud security, infrastructure reliability, and compliance with global standards.
End-to-End Encrypted Communication
All data between D-ECS servers and M2M devices is protected with TLS/SSL encryption to safeguard device management and network integrity.
Encrypted Web Access
Client access to D-ECS is secured via HTTPS connections and Access Token authentication, ensuring private and authenticated communication at all times.
Scalability
Effortless Network Expansions
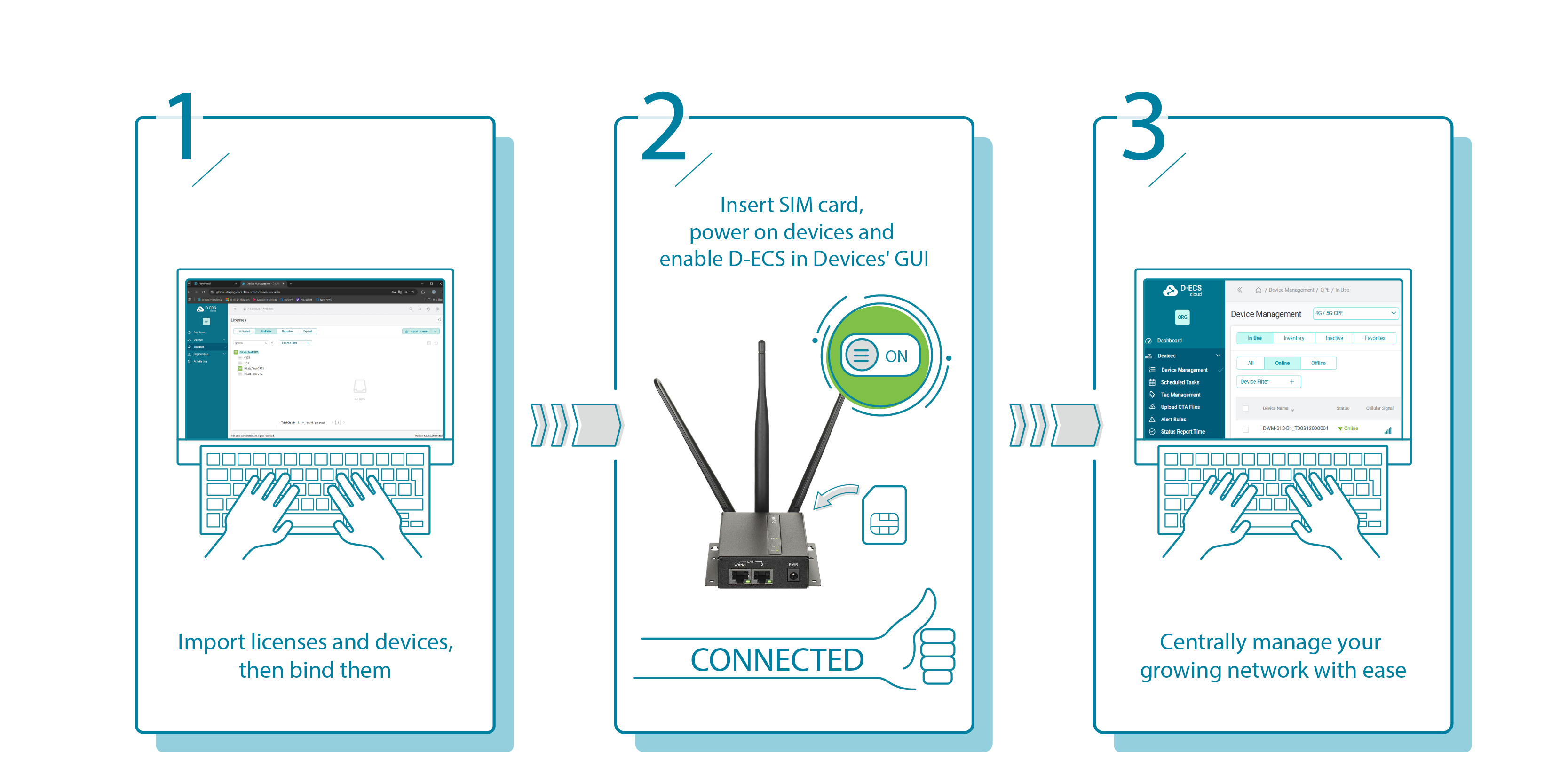
Set up devices quickly in just 3 simple steps, minimizing configuration time and effort for fast rollouts
Batch Device Onboarding & Configuration Deployment
Streamline large-scale deployments by importing licenses and devices in bulk. Deploy full configuration files simultaneously to one or multiple devices to streamline setups, ensure consistency, and reduce rollout time.
Unlimited Scalability
Easily expand your network with no device limits. Monitor, configure, and manage devices anytime, anywhere for ultimate flexibility.
Unlock the Full Potential of Your M2M Devices
Maximize your investment with D-ECS, D-Link’s cloud-based remote management platform. Start your free 90-day trial today and manage one of your existing 4G/5G M2M devices remotely—no complex setup required. See how easy it is to streamline your network operations—watch the D-ECS tutorial video and start your free trial today!
M2M Device Remote Management
Managing and supporting M2M devices remotely shouldn’t be complicated. With D-ECS, D-Link’s cloud-based platform, you can manage, monitor, and troubleshoot your 4G/5G M2M devices anytime, anywhere—no complex remote access setup required. Streamline operations, reduce downtime, and improve customer service effortlessly.

Already Have D-Link M2M Devices?
If you‘ve already deployed D-Link M2M devices but haven’t tried D-ECS yet, now’s the perfect time. Apply for a free 90-day trial and experience how D-Link’s remote management platform can optimize device management, boost operational efficiency, and scale your business faster.
Not Using D-Link M2M Devices Yet?
Even if you don't yet own D-Link M2M devices, you're welcome to explore D-ECS with our free test drive. Get hands-on experience with D-Link’s remote management platform and see how it can simplify device operations—and inspire your next smart solution purchase.
Start Your Journey with D-ECS
Experience seamless 4G/5G M2M device network management with D-ECS. Click the button below to explore the full range of D-ECS features and see how it can optimize your business operations.
Note: The demo account provides view-only access to dashboards, device status, and details. Operational functions—such as device configuration, diagnostics, performing actions, or adding devices and users—are not available in demo mode. For full feature access, please apply for the 90-day free trial.

